
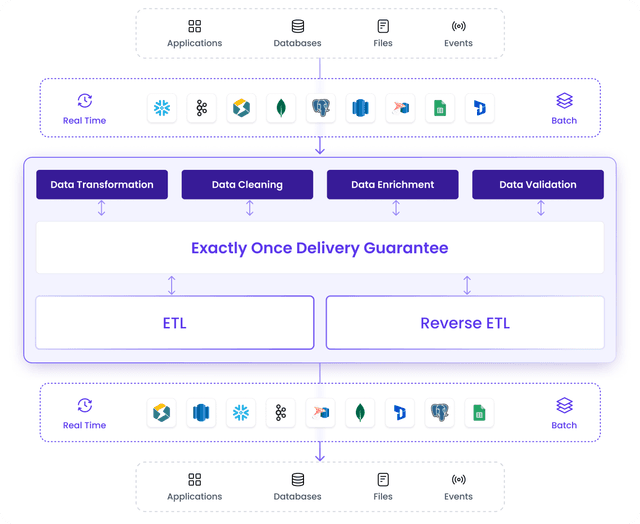
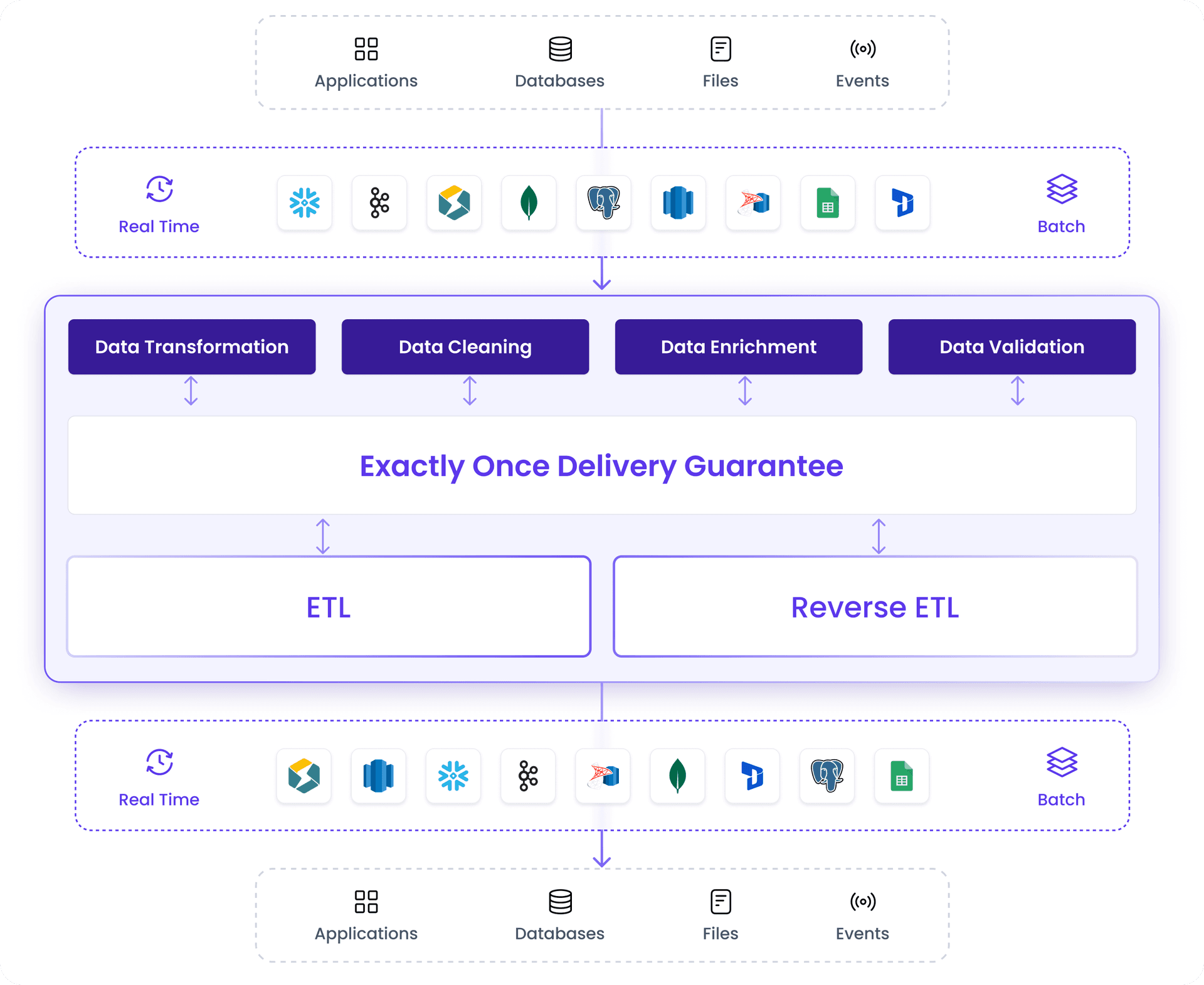
Reliable data pipelines with exactly once delivery
End to End Pipeline Automation
ETL and Reverse ETL on a single platform
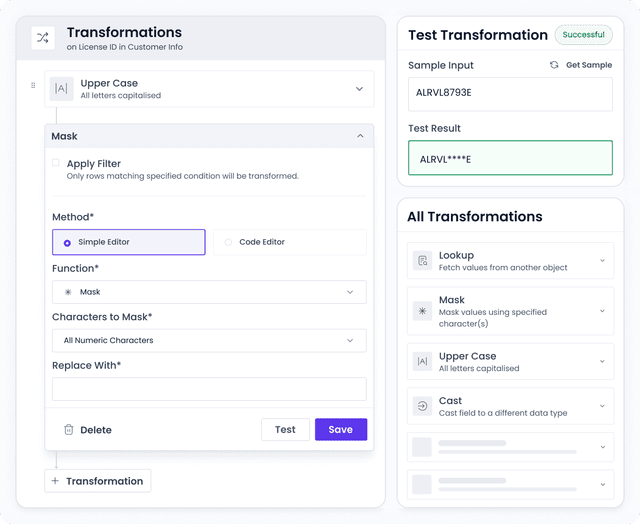
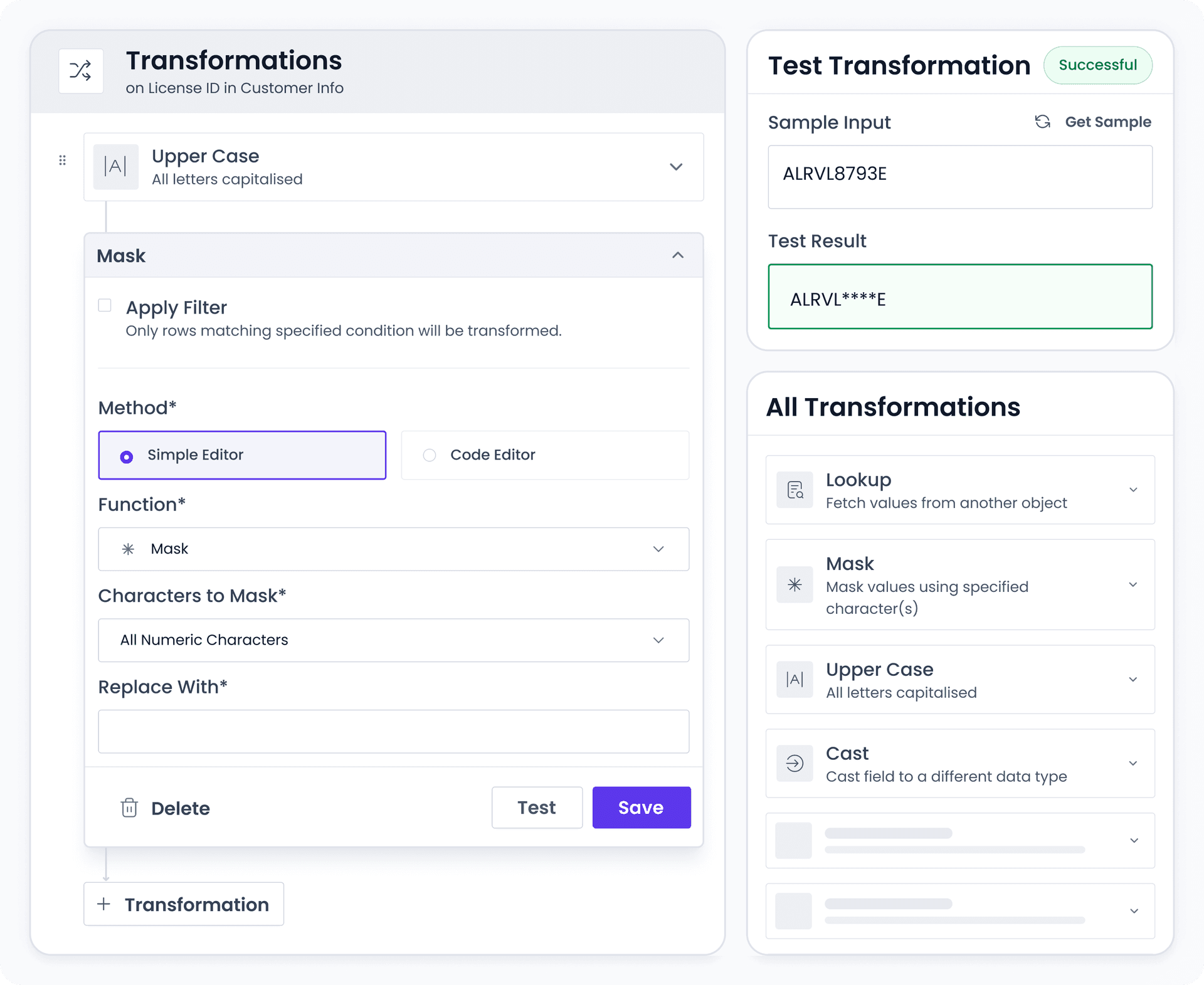
Data Transformations
Standardize data without impacting load performance with both pre and post load transformations
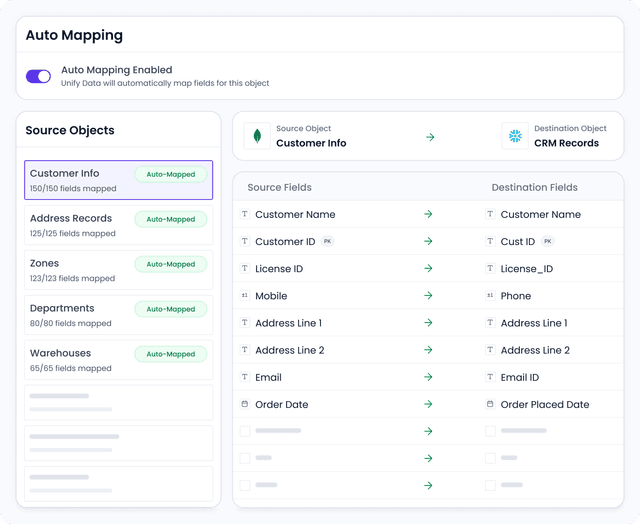
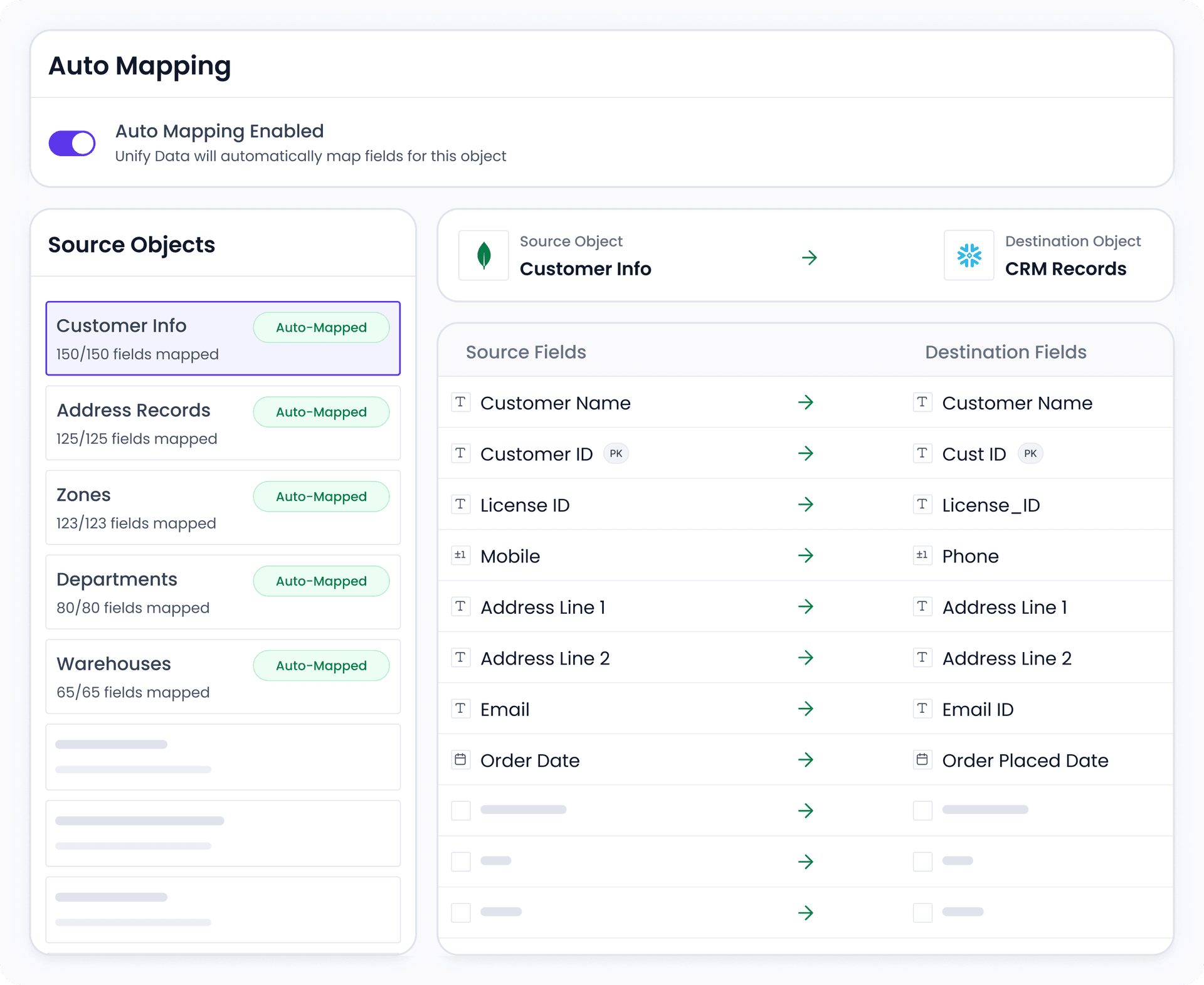
Automated Schema Management
Map fields from source schema to destination with minimal manual intervention

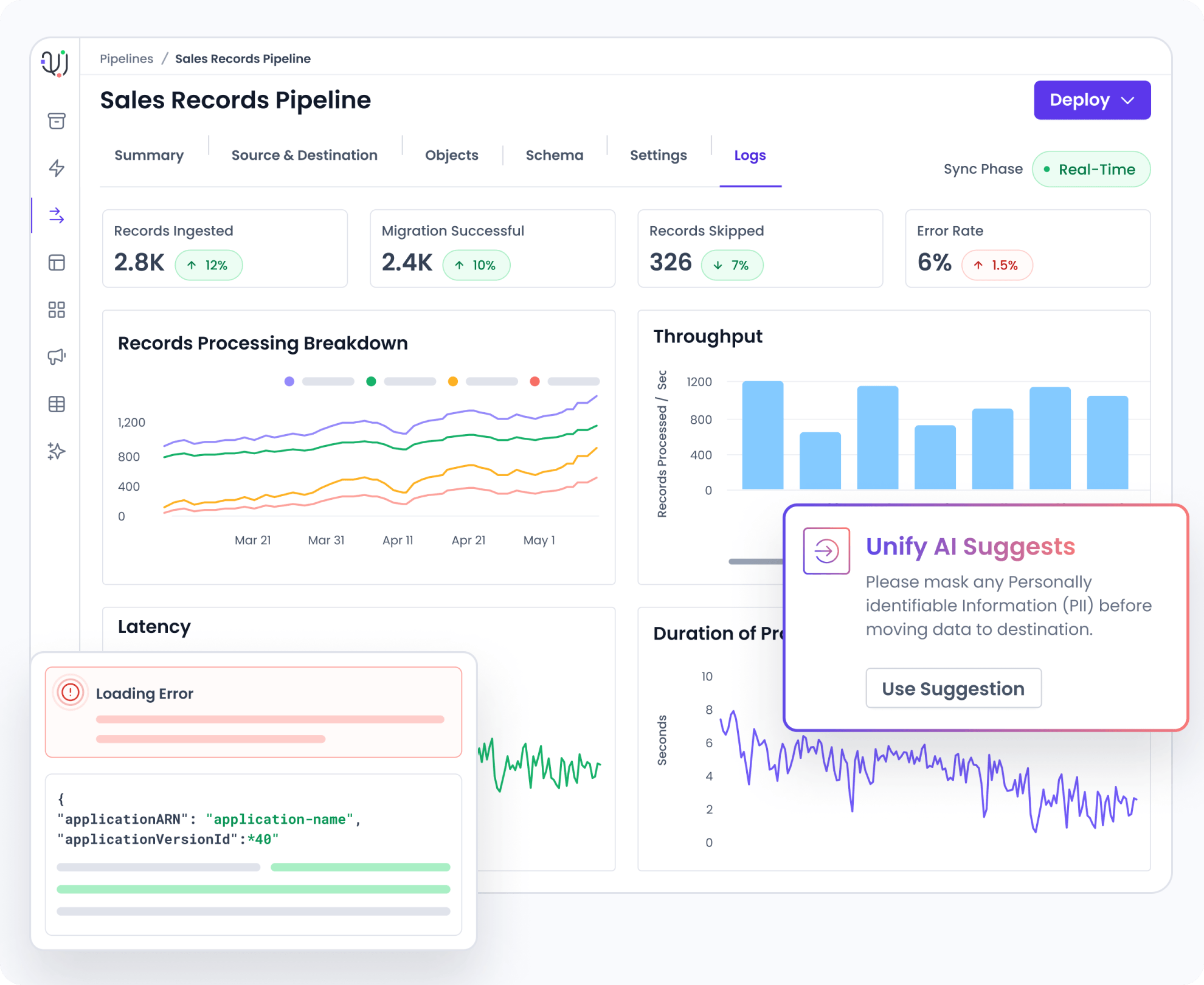
Monitor data movement across your entire platform
Comprehensive Error logs Identifying and debug issues proactively with real time alerts ensuring robust system resilience.
Real Time Monitoring Provide visibility into complete data pipeline activities, including extraction, loading, and transformation processes.
Automatic PII detection Mask Personally Identifiable Information within data flows to ensure data privacy and compliance with regulations.
Our products
.png&w=8192&q=75)













