Introduction
Data masking transformations can be used to protect sensitive information by replacing it with fictitious but realistic data. This process helps maintain data privacy while preserving the data's utility for development, testing, or analytical purposes.
Why Use Data Masking?
Risk Reduction: Minimize the risk of data breaches in non-production environments.
Data Privacy: Protect individual privacy while maintaining data utility.
Testing and Development: Use realistic data without exposing sensitive information.

Tip
Before implementing data masking, conduct a thorough data audit to identify all sensitive information across your systems.
Applying Mask Transformation
Follow these steps to apply the mask transformation:
Select "
Mask" from the list of Functions.Choose the "
Characters to Mask" based on your requirements.Configure additional options as needed.
Select a replacement character in the "
Replace With" field.Click "
Save" to apply the transformation.

Tip
When choosing a replacement character, consider using one that maintains the visual length of the original data to prevent layout issues in applications.
Masking Options
Various masking options are available to cater to different data protection needs:
All Characters
Effect: Masks every character in the string.
Example: "Abc12DE456" becomes "xxxxxxxxxx"
Use Case: When complete obfuscation is required.
.png&w=1080&q=75)
.png)
All Numeric Characters
Effect: Masks only the numeric characters.
Example: "Abc12DE456" becomes "AbcxxDExxx"
Use Case: Protecting numeric data like account numbers.
.png&w=1080&q=75)
.png)
Tip
For numeric data, consider using consistent replacement digits (e.g., all 9's or 0's) to maintain data type integrity.
All Special Characters
Effect: Masks special characters while preserving alphanumeric content.
Example: "AB12#$aba" becomes "AB12xxaba"
Use Case: Hiding specific markers or separators in data.
.png&w=1080&q=75)
.png)
All Alphabetic Characters
Effect: Masks alphabetic characters, leaving numbers and special characters intact.
Example: "AB12CD34#$" becomes "xx12xx34#$"
Use Case: Obscuring names or text while preserving numeric data.
.png&w=1080&q=75)
.png)
First Few Characters
Effect: Masks a specified number of characters from the beginning.
Configuration: Enter the "Number of Characters to Mask"
Example: "AB12CD34#$" becomes "xxxCD34#$" (masking first 3 characters)
Use Case: Partially obscuring identifiers while leaving some visible.
.png&w=1080&q=75)
.png)
Tip
When masking partial strings, ensure that the remaining visible portion doesn't inadvertently reveal sensitive information.
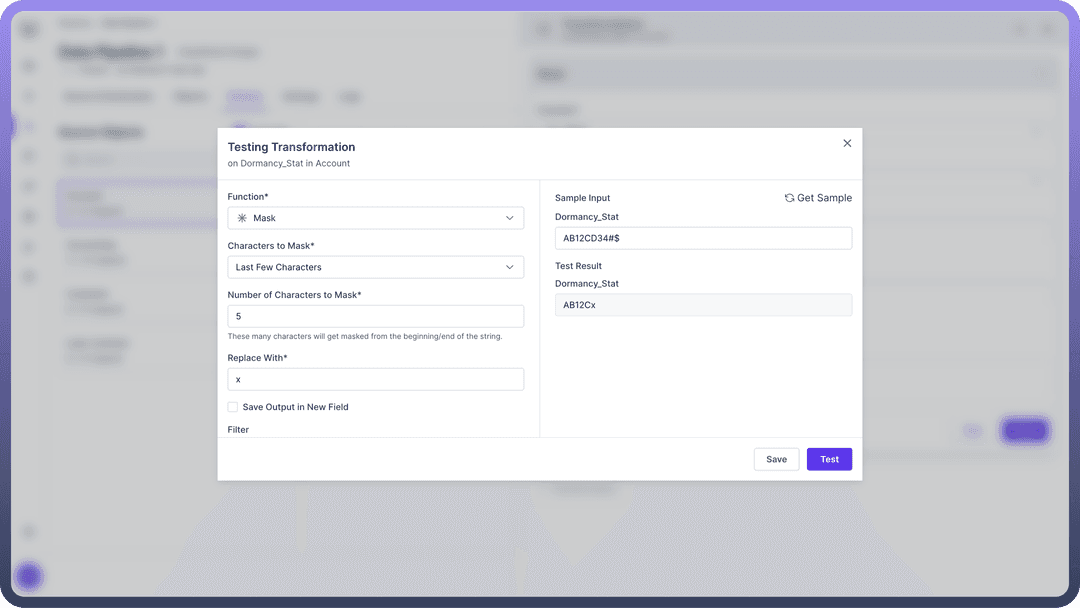
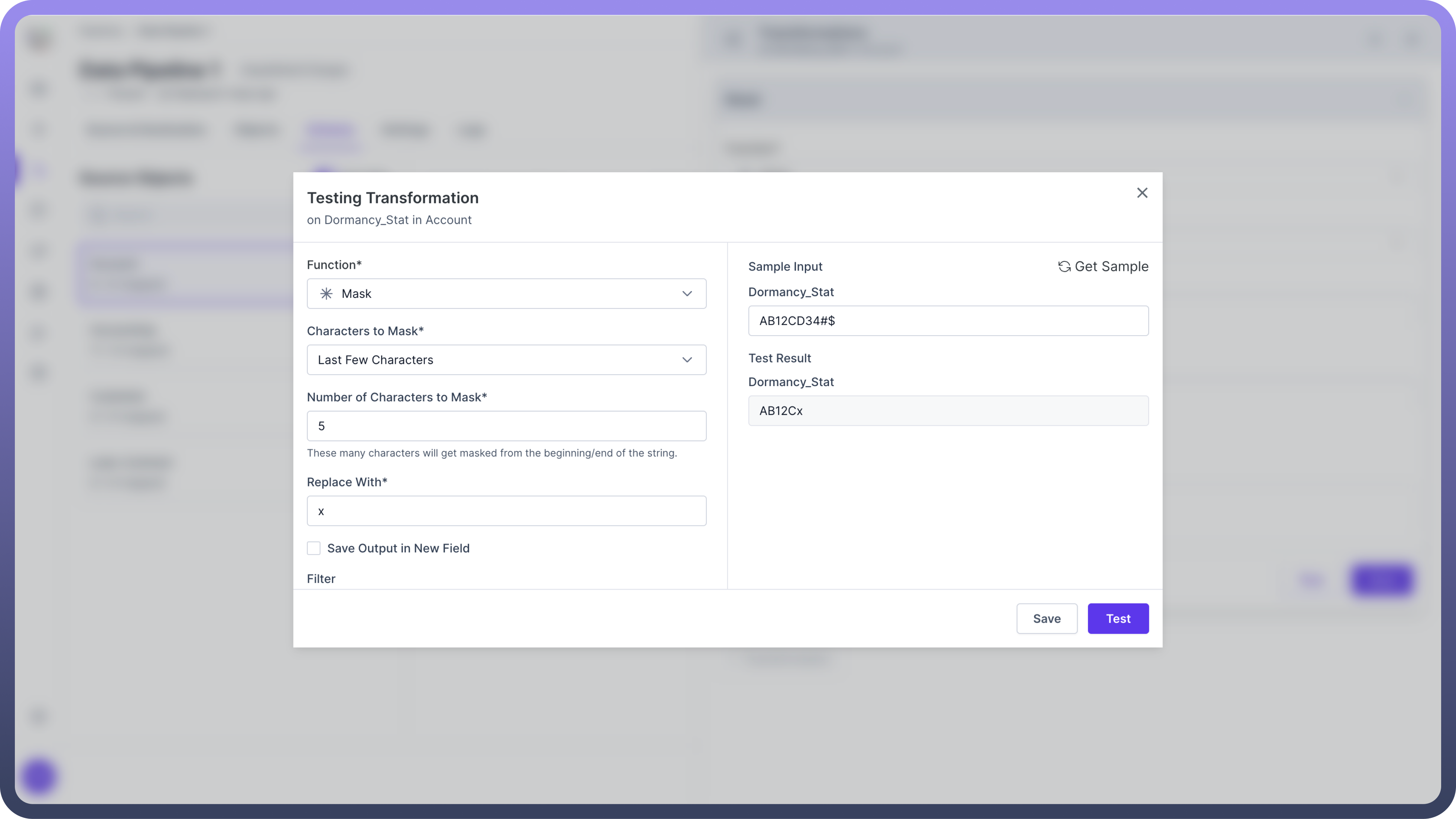
Last Few Characters
Effect: Masks a specified number of characters from the end.
Configuration: Enter the "Number of Characters to Mask"
Example: "AB12CD34#$" becomes "AB12CDxxx" (masking last 3 characters)
Use Case: Hiding sensitive suffixes like domain names in email addresses.
Exact Match
Effect: Masks a specific substring within the data.
Configuration: Enter the exact "String to Match"
Example: "AB12CD34#$" becomes "ABxxxx34#$" (masking "12CD")
Use Case: Targeting specific known sensitive data patterns.
.png&w=1080&q=75)
.png)
Use Regular Expression
Effect: Masks parts of the string that match a given regular expression.
Configuration: Enter a regular expression pattern
Example: "\d{4}" could mask any four-digit number in the string
Use Case: Advanced pattern-based masking for complex data structures.

Tip
Test your regular expressions thoroughly on a sample dataset before applying them to your entire database to ensure they catch all intended patterns without over-masking.
Best Practices
Consistency: Use consistent masking across related data fields.
Realism: Choose masking techniques that preserve the look and feel of the original data.
Comprehensive Coverage: Identify all instances of sensitive data, including derived fields.
Documentation: Maintain clear documentation of masking rules and processes.

Tip
Regularly review and update your masking rules to account for new types of sensitive data or changes in data structures.